-
We've added an example prompt to help you get started with building AI agents and applications on Cloudflare Workers, including Workflows, Durable Objects, and Workers KV.
You can use this prompt with your favorite AI model, including Claude 3.5 Sonnet, OpenAI's o3-mini, Gemini 2.0 Flash, or Llama 3.3 on Workers AI. Models with large context windows will allow you to paste the prompt directly: provide your own prompt within the
<user_prompt></user_prompt>tags.Terminal window {paste_prompt_here}<user_prompt>user: Build an AI agent using Cloudflare Workflows. The Workflow should run when a new GitHub issue is opened on a specific project with the label 'help' or 'bug', and attempt to help the user troubleshoot the issue by calling the OpenAI API with the issue title and description, and a clear, structured prompt that asks the model to suggest 1-3 possible solutions to the issue. Any code snippets should be formatted in Markdown code blocks. Documentation and sources should be referenced at the bottom of the response. The agent should then post the response to the GitHub issue. The agent should run as the provided GitHub bot account.</user_prompt>This prompt is still experimental, but we encourage you to try it out and provide feedback ↗.
-
Super Slurper now transfers data from cloud object storage providers like AWS S3 and Google Cloud Storage to Cloudflare R2 up to 5x faster than it did before.
We moved from a centralized service to a distributed system built on the Cloudflare Developer Platform — using Cloudflare Workers, Durable Objects, and Queues — to both improve performance and increase system concurrency capabilities (and we'll share more details about how we did it soon!)
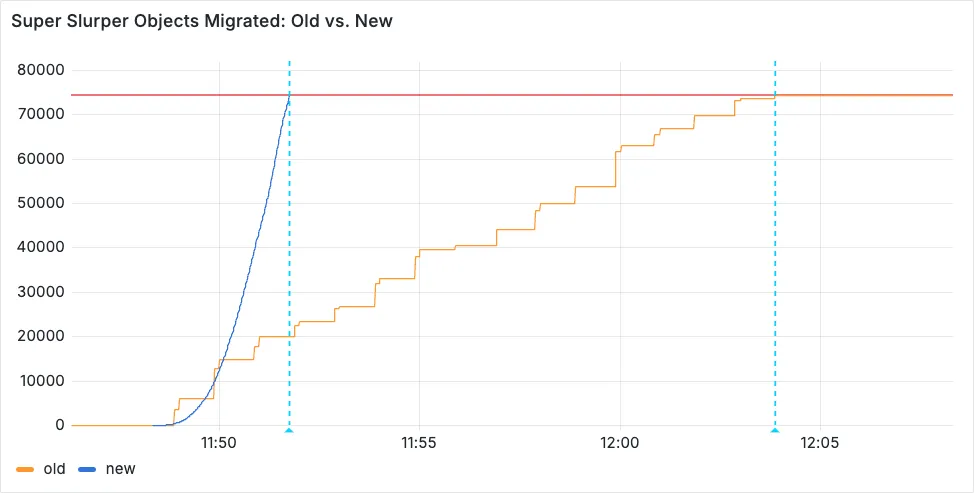
Time to copy 75,000 objects from AWS S3 to R2 decreased from 15 minutes 30 seconds (old) to 3 minutes 25 seconds (after performance improvements)
For more information on Super Slurper and how to migrate data from existing object storage to R2, refer to our documentation.
-
You can now customize a queue's message retention period, from a minimum of 60 seconds to a maximum of 14 days. Previously, it was fixed to the default of 4 days.
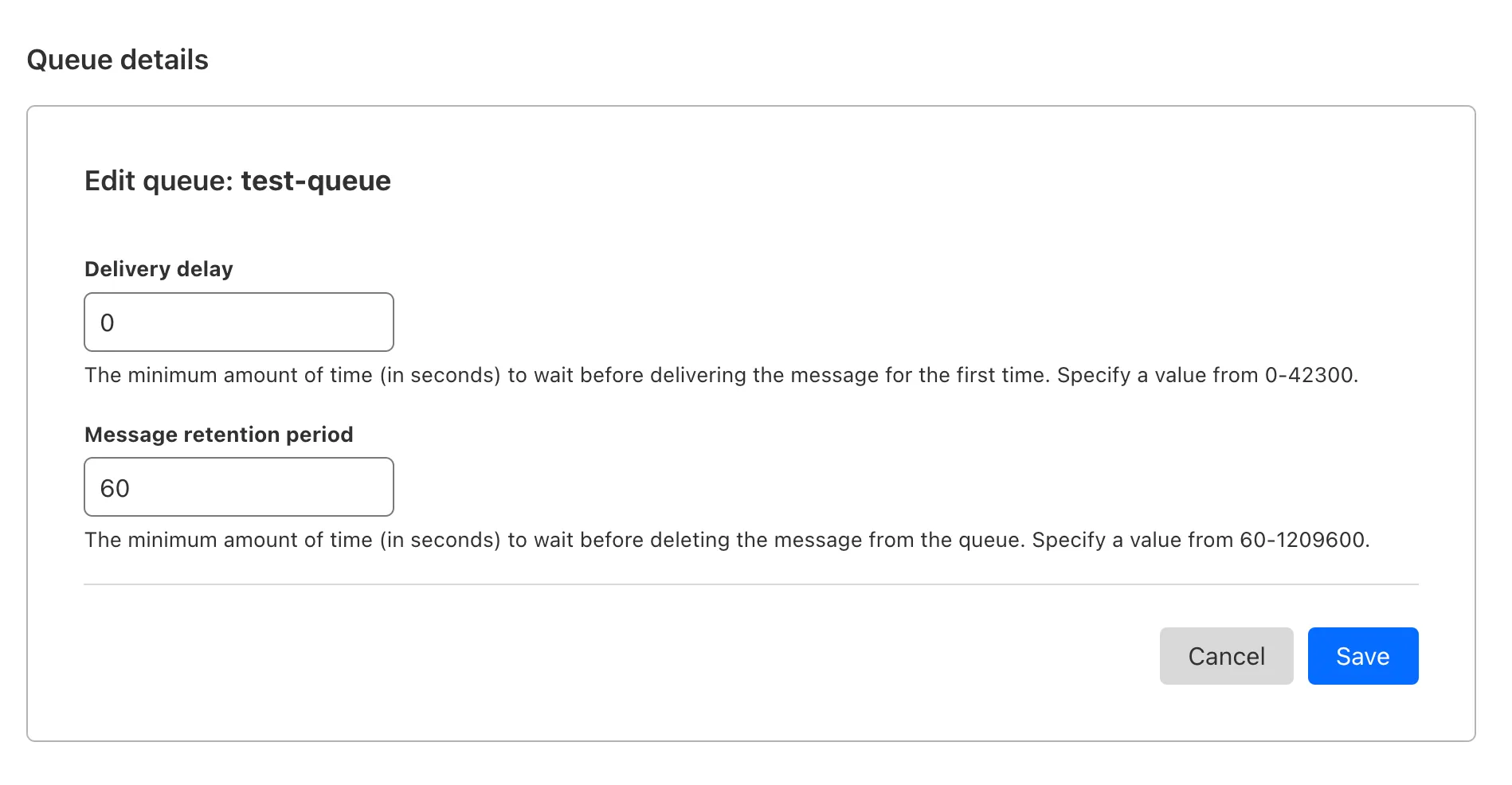
You can customize the retention period on the settings page for your queue, or using Wrangler:
Update message retention period $ wrangler queues update my-queue --message-retention-period-secs 600This feature is available on all new and existing queues. If you haven't used Cloudflare Queues before, get started with the Cloudflare Queues guide.
-
Previously, all viewers watched "the live edge," or the latest content of the broadcast, synchronously. If a viewer paused for more than a few seconds, the player would automatically "catch up" when playback started again. Seeking through the broadcast was only available once the recording was available after it conluded.
Starting today, customers can make a small adjustment to the player embed or manifest URL to enable the DVR experience for their viewers. By offering this feature as an opt-in adjustment, our customers are empowered to pick the best experiences for their applications.
When building a player embed code or manifest URL, just add
dvrEnabled=trueas a query parameter. There are some things to be aware of when using this option. For more information, refer to DVR for Live.
-
We have upgraded and streamlined Cloudflare Rules limits across all plans, simplifying rule management and improving scalability for everyone.
New limits by product:
- Bulk Redirects
- Free: 20 → 10,000 URL redirects across lists
- Pro: 500 → 25,000 URL redirects across lists
- Business: 500 → 50,000 URL redirects across lists
- Enterprise: 10,000 → 1,000,000 URL redirects across lists
- Cloud Connector
- Free: 5 → 10 connectors
- Enterprise: 125 → 300 connectors
- Custom Errors
- Pro: 5 → 25 error assets and rules
- Business: 20 → 50 error assets and rules
- Enterprise: 50 → 300 error assets and rules
- Snippets
- Pro: 10 → 25 code snippets and rules
- Business: 25 → 50 code snippets and rules
- Enterprise: 50 → 300 code snippets and rules
- Cache Rules, Configuration Rules, Compression Rules, Origin Rules, Single Redirects, and Transform Rules
- Enterprise: 125 → 300 rules
- Bulk Redirects
-
You can now filter Access policies by their action, selectors, rule groups, and assigned applications.
Private self-hosted applications and reusable Access policies are now generally available (GA) for all customers.
Cloudflare Access self-hosted applications can now be defined by private IPs, private hostnames (on port 443) and public hostnames. Additionally, we made Access policies into their own object which can be reused across multiple applications. These updates involved significant updates to the overall Access dashboard experience. The updates will be slowly rolled out to different customer cohorts. If you are an Enterprise customer and would like early access, reach out to your account team.
Enterprise customers can now use Logpush to export SSH command logs for Access for Infrastructure targets.
-
We're introducing Custom Errors (beta), which builds on our existing Custom Error Responses feature with new asset storage capabilities.
This update allows you to store externally hosted error pages on Cloudflare and reference them in custom error rules, eliminating the need to supply inline content.
This brings the following new capabilities:
- Custom error assets – Fetch and store external error pages at the edge for use in error responses.
- Account-Level custom errors – Define error handling rules and assets at the account level for consistency across multiple zones. Zone-level rules take precedence over account-level ones, and assets are not shared between levels.
You can use Cloudflare API to upload your existing assets for use with Custom Errors:
Terminal window curl "https://api.cloudflare.com/client/v4/zones/{zone_id}/custom_pages/assets" \--header "Authorization: Bearer <API_TOKEN>" \--header 'Content-Type: application/json' \--data '{"name": "maintenance","description": "Maintenance template page","url": "https://example.com/"}'You can then reference the stored asset in a Custom Error rule:
Terminal window curl --request PUT \"https://api.cloudflare.com/client/v4/zones/{zone_id}/rulesets/phases/http_custom_errors/entrypoint" \--header "Authorization: Bearer <API_TOKEN>" \--header 'Content-Type: application/json' \--data '{"rules": [{"action": "serve_error","action_parameters": {"asset_name": "maintenance","content_type": "text/html","status_code": 503},"enabled": true,"expression": "http.request.uri.path contains \"error\""}]}'
-
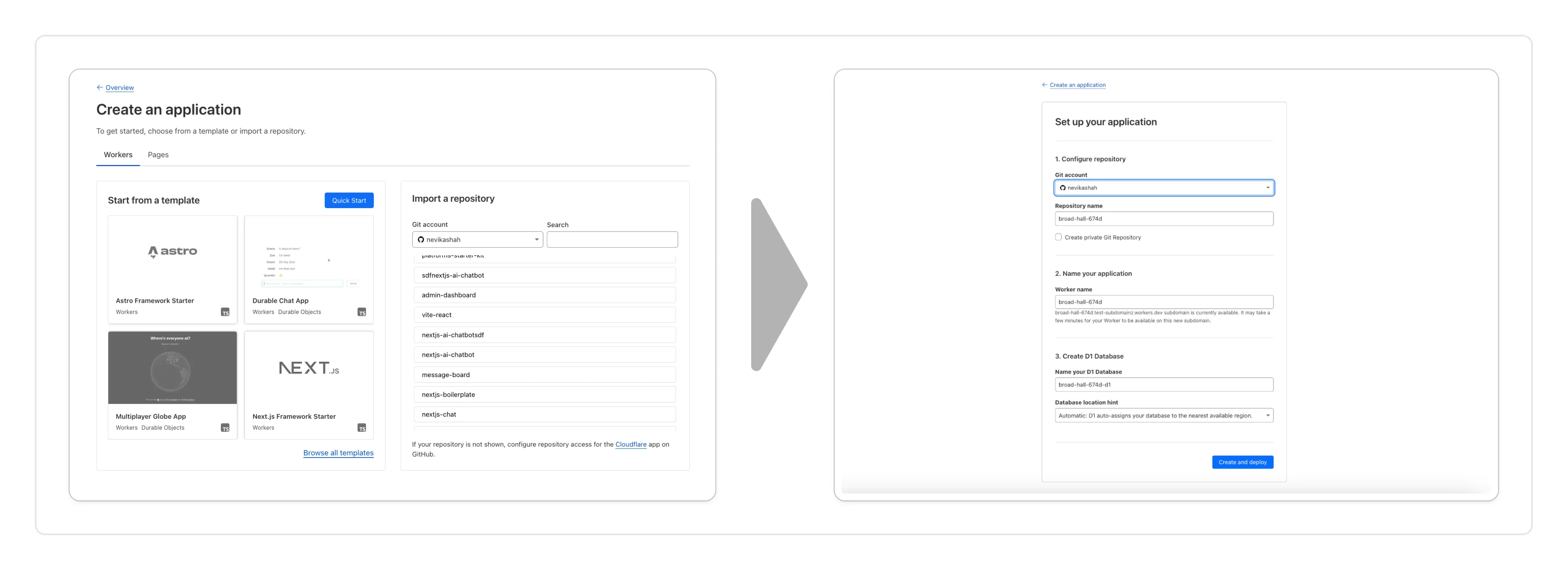
You can now create a Worker by:
- Importing a Git repository: Choose an existing Git repo on your GitHub/GitLab account and set up Workers Builds to deploy your Worker.
- Deploying a template with Git: Choose from a brand new selection of production ready examples ↗ to help you get started with popular frameworks like Astro ↗, Remix ↗ and Next ↗ or build stateful applications with Cloudflare resources like D1 databases, Workers AI or Durable Objects! When you're ready to deploy, Cloudflare will set up your project by cloning the template to your GitHub/GitLab account, provisioning any required resources and deploying your Worker.
With every push to your chosen branch, Cloudflare will automatically build and deploy your Worker.
To get started, go to the Workers dashboard ↗.
These new features are available today in the Cloudflare dashboard to a subset of Cloudflare customers, and will be coming to all customers in the next few weeks. Don't see it in your dashboard, but want early access? Add your Cloudflare Account ID to this form ↗.
-
AI Gateway adds additional ways to handle requests - Request Timeouts and Request Retries, making it easier to keep your applications responsive and reliable.
Timeouts and retries can be used on both the Universal Endpoint or directly to a supported provider.
Request timeouts A request timeout allows you to trigger fallbacks or a retry if a provider takes too long to respond.
To set a request timeout directly to a provider, add a
cf-aig-request-timeoutheader.Provider-specific endpoint example curl https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/workers-ai/@cf/meta/llama-3.1-8b-instruct \--header 'Authorization: Bearer {cf_api_token}' \--header 'Content-Type: application/json' \--header 'cf-aig-request-timeout: 5000'--data '{"prompt": "What is Cloudflare?"}'Request retries A request retry automatically retries failed requests, so you can recover from temporary issues without intervening.
To set up request retries directly to a provider, add the following headers:
- cf-aig-max-attempts (number)
- cf-aig-retry-delay (number)
- cf-aig-backoff ("constant" | "linear" | "exponential)
-
AI Gateway has added three new providers: Cartesia, Cerebras, and ElevenLabs, giving you more even more options for providers you can use through AI Gateway. Here's a brief overview of each:
- Cartesia provides text-to-speech models that produce natural-sounding speech with low latency.
- Cerebras delivers low-latency AI inference to Meta's Llama 3.1 8B and Llama 3.3 70B models.
- ElevenLabs offers text-to-speech models with human-like voices in 32 languages.

To get started with AI Gateway, just update the base URL. Here's how you can send a request to Cerebras using cURL:
Example fetch request curl -X POST https://gateway.ai.cloudflare.com/v1/ACCOUNT_TAG/GATEWAY/cerebras/chat/completions \--header 'content-type: application/json' \--header 'Authorization: Bearer CEREBRAS_TOKEN' \--data '{"model": "llama-3.3-70b","messages": [{"role": "user","content": "What is Cloudflare?"}]}'
-
You can now implement our child safety tooling, the CSAM Scanning Tool, more easily. Instead of requiring external reporting credentials, you only need a verified email address for notifications to onboard. This change makes the tool more accessible to a wider range of customers.
When enabled, the tool automatically hashes images for enabled websites as they enter the Cloudflare cache ↗. These hashes are then checked against a database of known abusive images.
- Potential match detected?
- The content URL is blocked, and
- Cloudflare will notify you about the found matches via the provided email address.
We have also made updates to our Service-Specific Terms ↗ to reflect these changes.
- Potential match detected?
-
Radar has expanded its AI insights with new API endpoints for Internet services rankings, robots.txt analysis, and AI inference data.
Radar now provides rankings for Internet services, including Generative AI platforms, based on anonymized 1.1.1.1 resolver data. Previously limited to the annual Year in Review, these insights are now available daily via the API, through the following endpoints:
topshow service popularity at a specific date.timeseries_groupstrack ranking trends over time.
Radar now analyzes robots.txt files from the top 10,000 domains, identifying AI bot access rules. AI-focused user agents from ai.robots.txt ↗ are categorized as:
- Fully allowed/disallowed if directives apply to all paths (
*). - Partially allowed/disallowed if restrictions apply to specific paths.
These insights are now available weekly via the API, through the following endpoints:
top/user_agents/directiveto get the top AI user agents by directive.top/domain_categoriesto get the top domain categories by robots.txt files.
Radar now provides insights into public AI inference models from Workers AI, tracking usage trends across models and tasks. These insights are now available via the API, through the following endpoints:
summaryto view aggregatedmodelandtaskpopularity.timeseries_groupsto track changes over time formodelortask.
Learn more about the new Radar AI insights in our blog post ↗.
-
We've revamped the Workers Metrics dashboard ↗.
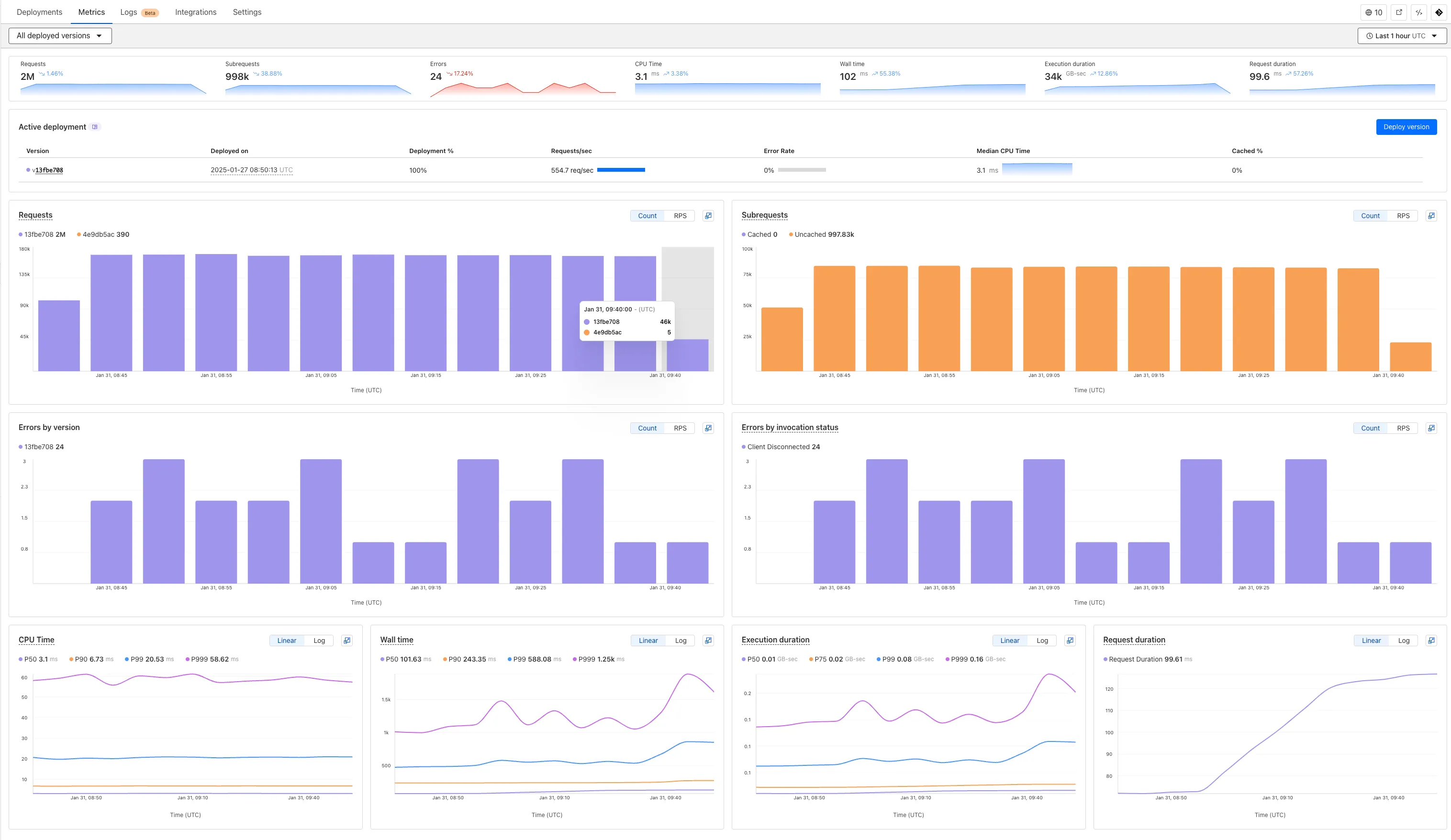
Now you can easily compare metrics across Worker versions, understand the current state of a gradual deployment, and review key Workers metrics in a single view. This new interface enables you to:
- Drag-and-select using a graphical timepicker for precise metric selection.
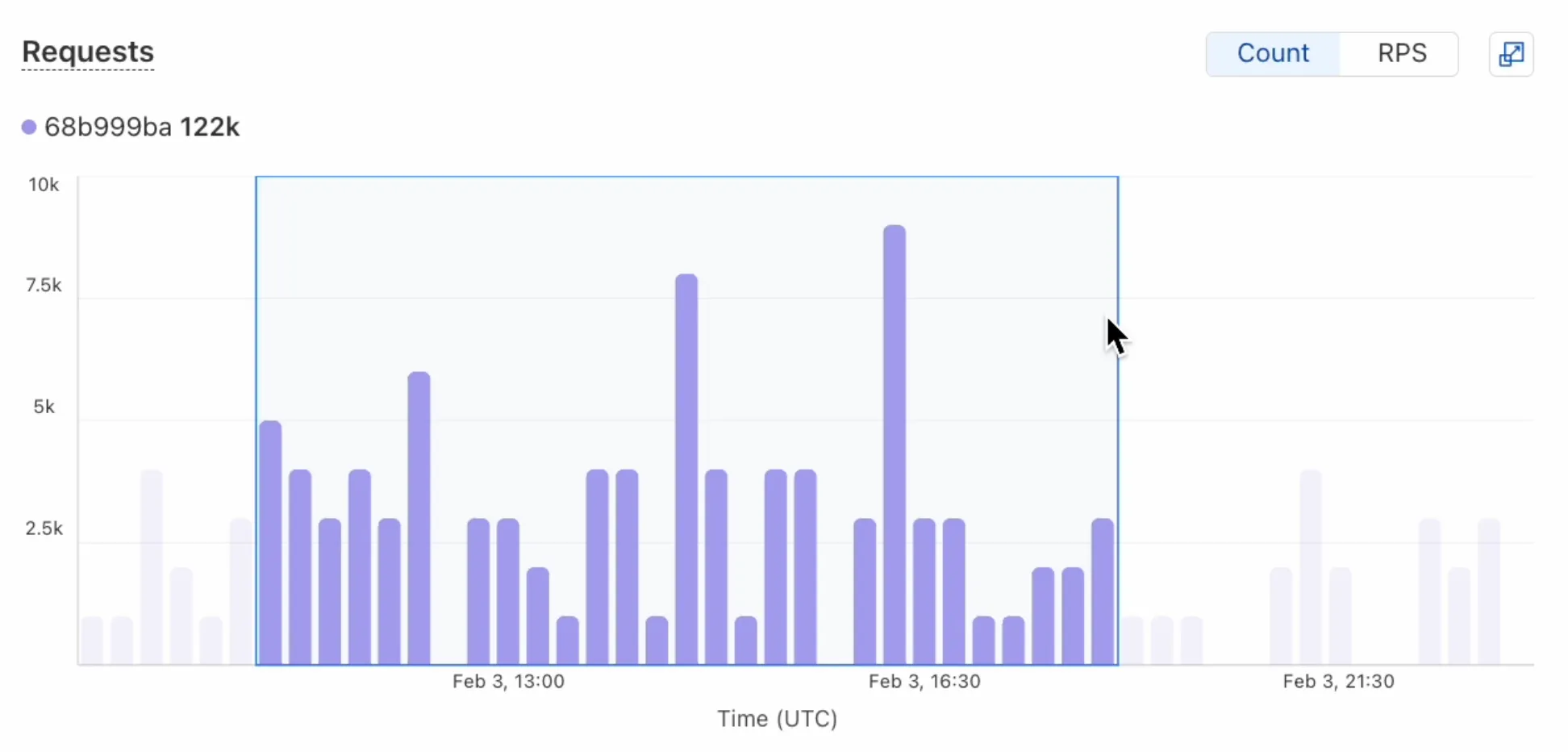
- Use histograms to visualize cumulative metrics, allowing you to bucket and compare rates over time.
- Focus on Worker versions by directly interacting with the version numbers in the legend.
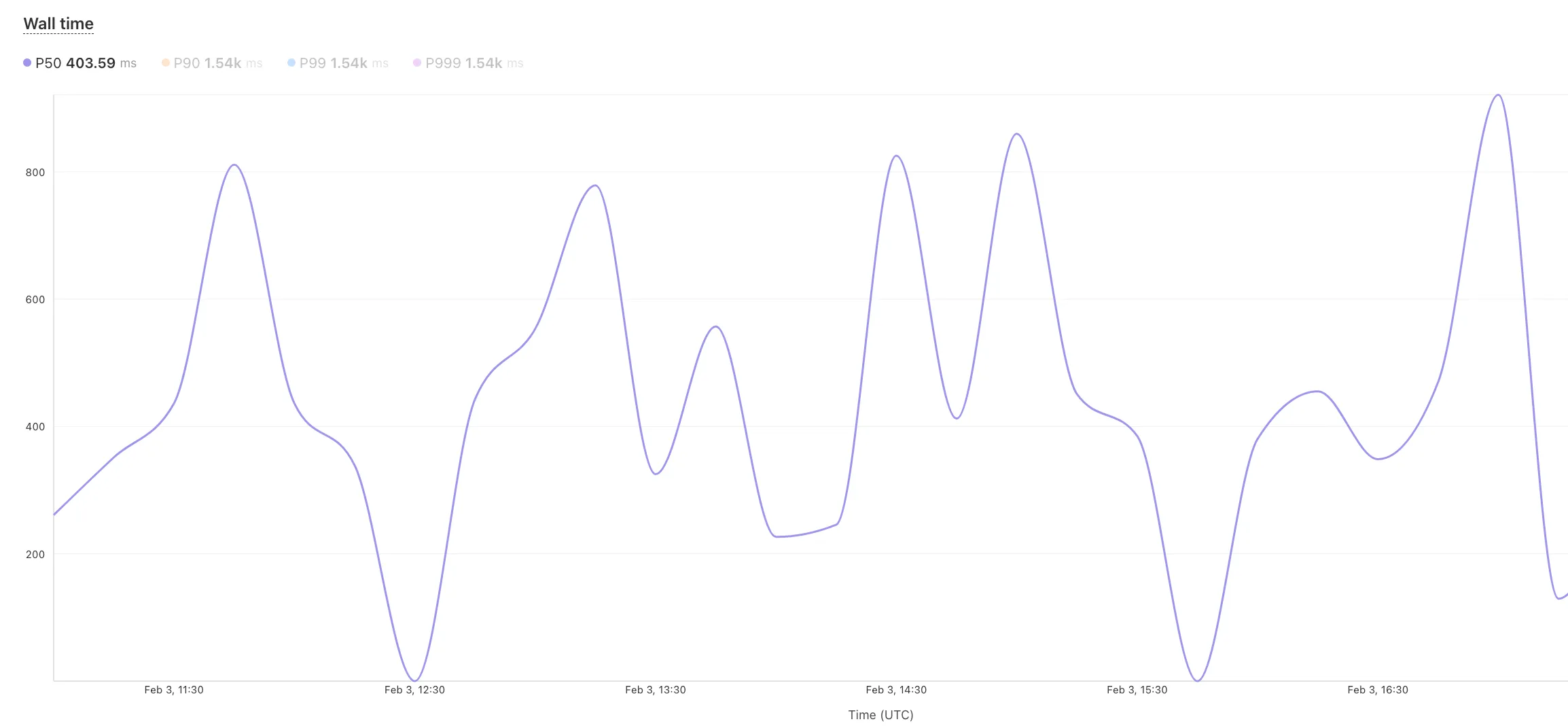
- Monitor and compare active gradual deployments.
- Track error rates across versions with grouping both by version and by invocation status.
- Measure how Smart Placement improves request duration.
Learn more about metrics.
-
Cloudflare's v5 Terraform Provider is now generally available. With this release, Terraform resources are now automatically generated based on OpenAPI Schemas. This change brings alignment across our SDKs, API documentation, and now Terraform Provider. The new provider boosts coverage by increasing support for API properties to 100%, adding 25% more resources, and more than 200 additional data sources. Going forward, this will also reduce the barriers to bringing more resources into Terraform across the broader Cloudflare API. This is a small, but important step to making more of our platform manageable through GitOps, making it easier for you to manage Cloudflare just like you do your other infrastructure.
The Cloudflare Terraform Provider v5 is a ground-up rewrite of the provider and introduces breaking changes for some resource types. Please refer to the upgrade guide ↗ for best practices, or the blog post on automatically generating Cloudflare's Terraform Provider ↗ for more information about the approach.
For more info
-
If you installed the default Cloudflare certificate before 2024-10-17, you must generate a new certificate and activate it for your Zero Trust organization to avoid inspection errors. Refer to Troubleshooting for instructions and troubleshooting steps.
Enterprise users can now provide an IP address for a private DNS resolver to use with DNS locations. Gateway supports bringing your own IPv4 and IPv6 addresses.
-
Workers for Platforms customers can now attach static assets (HTML, CSS, JavaScript, images) directly to User Workers, removing the need to host separate infrastructure to serve the assets.
This allows your platform to serve entire front-end applications from Cloudflare's global edge, utilizing caching for fast load times, while supporting dynamic logic within the same Worker. Cloudflare automatically scales its infrastructure to handle high traffic volumes, enabling you to focus on building features without managing servers.
Static Sites: Host and serve HTML, CSS, JavaScript, and media files directly from Cloudflare's network, ensuring fast loading times worldwide. This is ideal for blogs, landing pages, and documentation sites because static assets can be efficiently cached and delivered closer to the user, reducing latency and enhancing the overall user experience.
Full-Stack Applications: Combine asset hosting with Cloudflare Workers to power dynamic, interactive applications. If you're an e-commerce platform, you can serve your customers' product pages and run inventory checks from within the same Worker.
index.js export default {async fetch(request, env) {const url = new URL(request.url);// Check real-time inventoryif (url.pathname === "/api/inventory/check") {const product = url.searchParams.get("product");const inventory = await env.INVENTORY_KV.get(product);return new Response(inventory);}// Serve static assets (HTML, CSS, images)return env.ASSETS.fetch(request);},};index.ts export default {async fetch(request, env) {const url = new URL(request.url);// Check real-time inventoryif (url.pathname === '/api/inventory/check') {const product = url.searchParams.get('product');const inventory = await env.INVENTORY_KV.get(product);return new Response(inventory);}// Serve static assets (HTML, CSS, images)return env.ASSETS.fetch(request);}};Get Started: Upload static assets using the Workers for Platforms API or Wrangler. For more information, visit our Workers for Platforms documentation. ↗
-
You can now transform HTML elements with streamed content using
HTMLRewriter.Methods like
replace,append, andprependnow acceptResponseandReadableStreamvalues asContent.This can be helpful in a variety of situations. For instance, you may have a Worker in front of an origin, and want to replace an element with content from a different source. Prior to this change, you would have to load all of the content from the upstream URL and convert it into a string before replacing the element. This slowed down overall response times.
Now, you can pass the
Responseobject directly into thereplacemethod, and HTMLRewriter will immediately start replacing the content as it is streamed in. This makes responses faster.index.js class ElementRewriter {async element(element) {// able to replace elements while streaming content// the fetched body is not buffered into memory as part// of the replacelet res = await fetch("https://upstream-content-provider.example");element.replace(res);}}export default {async fetch(request, env, ctx) {let response = await fetch("https://site-to-replace.com");return new HTMLRewriter().on("[data-to-replace]", new ElementRewriter()).transform(response);},};index.ts class ElementRewriter {async element(element: any) {// able to replace elements while streaming content// the fetched body is not buffered into memory as part// of the replacelet res = await fetch('https://upstream-content-provider.example');element.replace(res);}}export default {async fetch(request, env, ctx): Promise<Response> {let response = await fetch('https://site-to-replace.com');return new HTMLRewriter().on('[data-to-replace]', new ElementRewriter()).transform(response);},} satisfies ExportedHandler<Env>;For more information, see the
HTMLRewriterdocumentation.
-
We have released new Workers bindings API methods, allowing you to connect Workers applications to AI Gateway directly. These methods simplify how Workers calls AI services behind your AI Gateway configurations, removing the need to use the REST API and manually authenticate.
To add an AI binding to your Worker, include the following in your Wrangler configuration file:
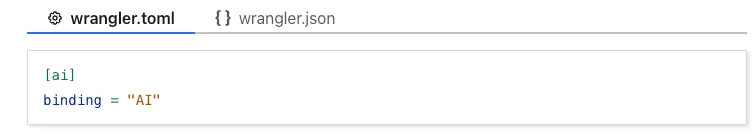
With the new AI Gateway binding methods, you can now:
- Send feedback and update metadata with
patchLog. - Retrieve detailed log information using
getLog. - Execute universal requests to any AI Gateway provider with
run.
For example, to send feedback and update metadata using
patchLog: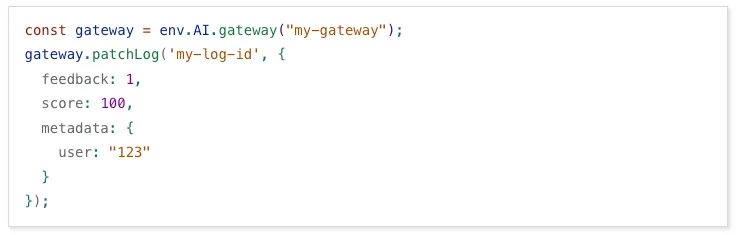
- Send feedback and update metadata with
-
Browser Rendering now supports 10 concurrent browser instances per account and 10 new instances per minute, up from the previous limits of 2.
This allows you to launch more browser tasks from Cloudflare Workers.
To manage concurrent browser sessions, you can use Queues or Workflows:
index.js export default {async queue(batch, env) {for (const message of batch.messages) {const browser = await puppeteer.launch(env.BROWSER);const page = await browser.newPage();try {await page.goto(message.url, {waitUntil: message.waitUntil,});// Process page...} finally {await browser.close();}}},};index.ts interface QueueMessage {url: string;waitUntil: number;}export interface Env {BROWSER_QUEUE: Queue<QueueMessage>;BROWSER: Fetcher;}export default {async queue(batch: MessageBatch<QueueMessage>, env: Env): Promise<void> {for (const message of batch.messages) {const browser = await puppeteer.launch(env.BROWSER);const page = await browser.newPage();try {await page.goto(message.url, {waitUntil: message.waitUntil});// Process page...} finally {await browser.close();}}}};
-
Stream's generated captions leverage Workers AI to automatically transcribe audio and provide captions to the player experience. We have added support for these languages:
cs- Czechnl- Dutchfr- Frenchde- Germanit- Italianja- Japaneseko- Koreanpl- Polishpt- Portugueseru- Russianes- Spanish
For more information, learn about adding captions to videos.
-
The new Snippets code editor lets you edit Snippet code and rule in one place, making it easier to test and deploy changes without switching between pages.
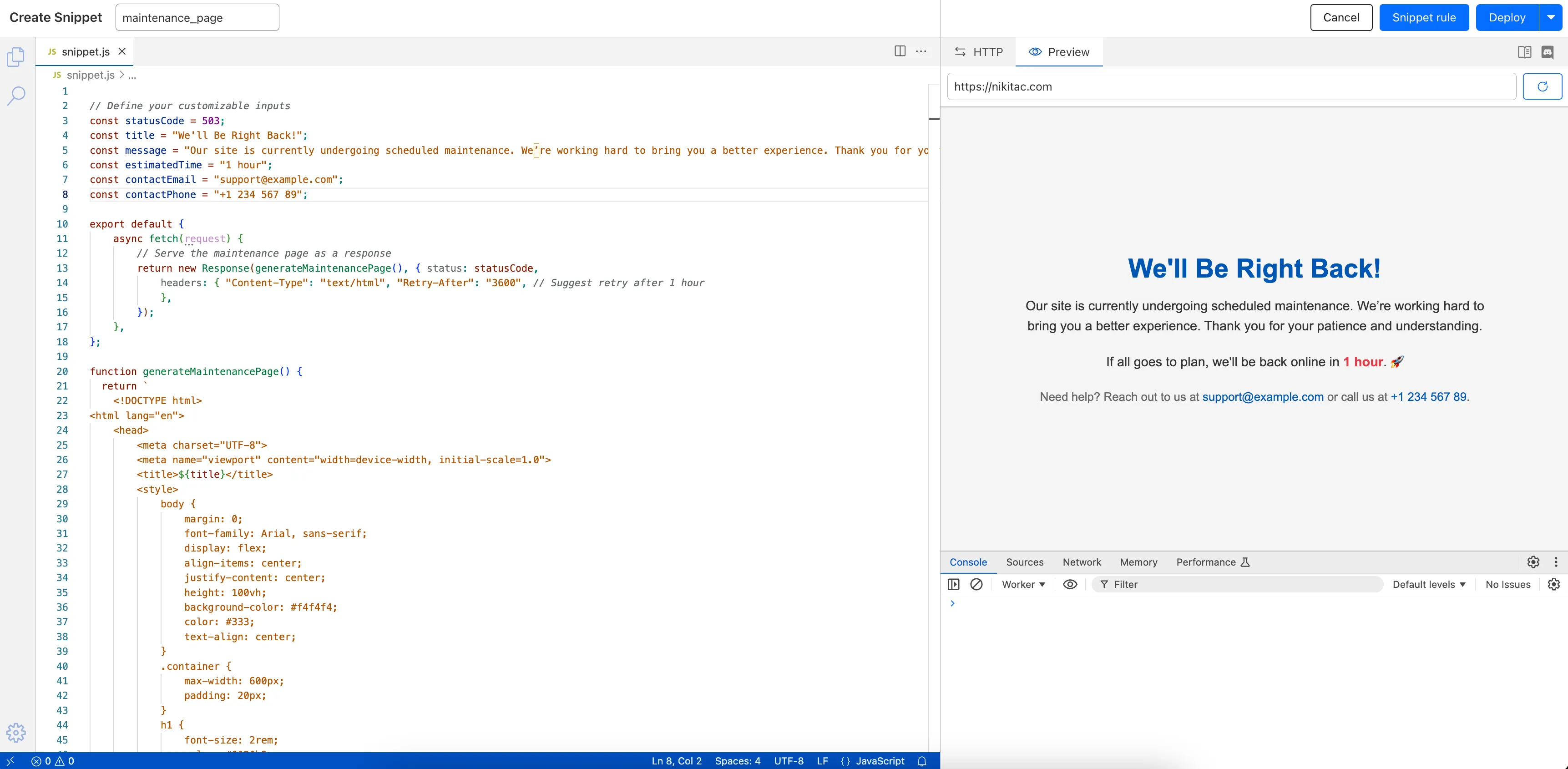
What’s new:
- Single-page editing for code and rule – No need to jump between screens.
- Auto-complete & syntax highlighting – Get suggestions and avoid mistakes.
- Code formatting & refactoring – Write cleaner, more readable code.
Try it now in Rules > Snippets ↗.
-
Hyperdrive now automatically configures your Cloudflare Tunnel to connect to your private database.
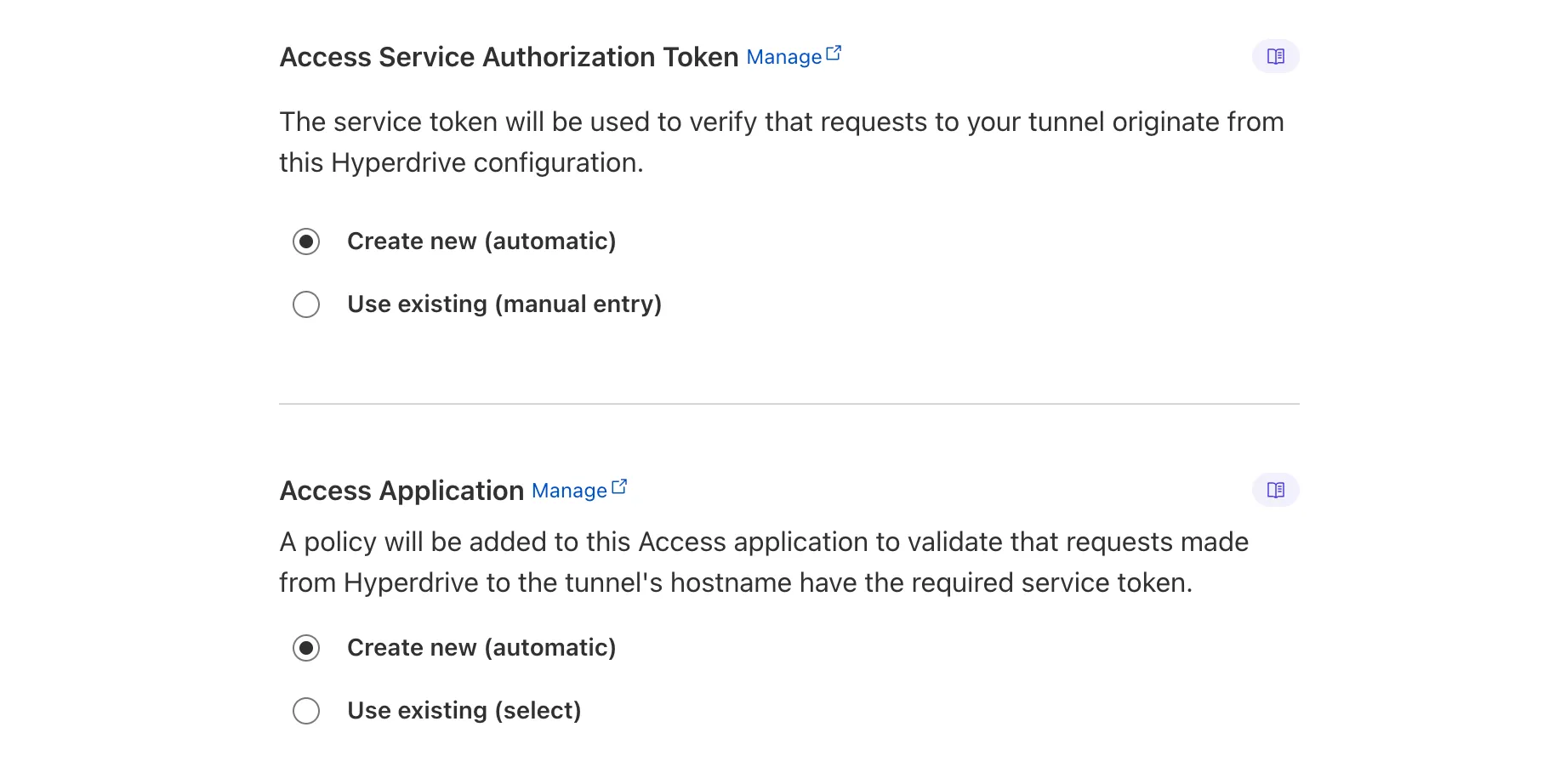
When creating a Hyperdrive configuration for a private database, you only need to provide your database credentials and set up a Cloudflare Tunnel within the private network where your database is accessible. Hyperdrive will automatically create the Cloudflare Access, Service Token, and Policies needed to secure and restrict your Cloudflare Tunnel to the Hyperdrive configuration.
To create a Hyperdrive for a private database, you can follow the Hyperdrive documentation. You can still manually create the Cloudflare Access, Service Token, and Policies if you prefer.
This feature is available from the Cloudflare dashboard.
-
You can now have up to 1000 Workers KV namespaces per account.
Workers KV namespace limits were increased from 200 to 1000 for all accounts. Higher limits for Workers KV namespaces enable better organization of key-value data, such as by category, tenant, or environment.
Consult the Workers KV limits documentation for the rest of the limits. This increased limit is available for both the Free and Paid Workers plans.
-
When using a Worker with the
nodejs_compatcompatibility flag enabled, you can now use the following Node.js APIs:You can use
node:net↗ to create a direct connection to servers via a TCP sockets withnet.Socket↗.index.js import net from "node:net";const exampleIP = "127.0.0.1";export default {async fetch(req) {const socket = new net.Socket();socket.connect(4000, exampleIP, function () {console.log("Connected");});socket.write("Hello, Server!");socket.end();return new Response("Wrote to server", { status: 200 });},};index.ts import net from "node:net";const exampleIP = "127.0.0.1";export default {async fetch(req): Promise<Response> {const socket = new net.Socket();socket.connect(4000, exampleIP, function () {console.log("Connected");});socket.write("Hello, Server!");socket.end();return new Response("Wrote to server", { status: 200 });},} satisfies ExportedHandler;Additionally, you can now use other APIs incliding
net.BlockList↗ andnet.SocketAddress↗.Note that
net.Server↗ is not supported.You can use
node:dns↗ for name resolution via DNS over HTTPS using Cloudflare DNS ↗ at 1.1.1.1.index.js import dns from "node:dns";let responese = await dns.promises.resolve4("cloudflare.com", "NS");index.ts import dns from 'node:dns';let responese = await dns.promises.resolve4('cloudflare.com', 'NS');All
node:dnsfunctions are available, exceptlookup,lookupService, andresolvewhich throw "Not implemented" errors when called.You can use
node:timers↗ to schedule functions to be called at some future period of time.This includes
setTimeout↗ for calling a function after a delay,setInterval↗ for calling a function repeatedly, andsetImmediate↗ for calling a function in the next iteration of the event loop.index.js import timers from "node:timers";console.log("first");timers.setTimeout(() => {console.log("last");}, 10);timers.setTimeout(() => {console.log("next");});index.ts import timers from "node:timers";console.log("first");timers.setTimeout(() => {console.log("last");}, 10);timers.setTimeout(() => {console.log("next");});
-
IP visibility enables admins to inspect the different IP addresses associated with an end-user device. IP types available for review on the Cloudflare dashboard include: the device's private IP, the public IP assigned to the device by the ISP, and the router's (that the device is connected to) private IP.
-
DLP now supports setting a confidence level for source code profiles.
When viewing decrypted payload log matches, DLP now provides more context by listing multiple DLP matches and the matching DLP profile.
-
Workflows (beta) now allows you to define up to 1024 steps.
sleepsteps do not count against this limit.We've also added:
instanceIdas property to theWorkflowEventtype, allowing you to retrieve the current instance ID from within a running Workflow instance- Improved queueing logic for Workflow instances beyond the current maximum concurrent instances, reducing the cases where instances are stuck in the queued state.
- Support for
pauseandresumefor Workflow instances in a queued state.
We're continuing to work on increases to the number of concurrent Workflow instances, steps, and support for a new
waitForEventAPI over the coming weeks.
-
Rules Overview gives you a single page to manage all your Cloudflare Rules.
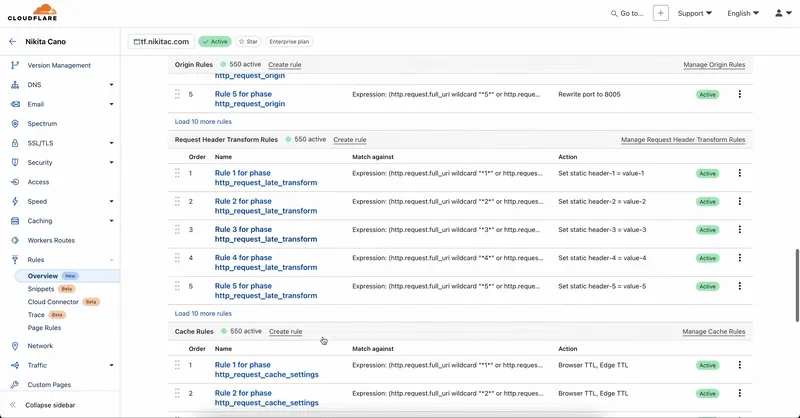
What you can do:
- See all your rules in one place – No more clicking around.
- Find rules faster – Search by name.
- Understand execution order – See how rules run in sequence.
- Debug easily – Use Trace without switching tabs.
Check it out in Rules > Overview ↗.
-
Users making D1 requests via the Workers API can see up to a 60% end-to-end latency improvement due to the removal of redundant network round trips needed for each request to a D1 database.
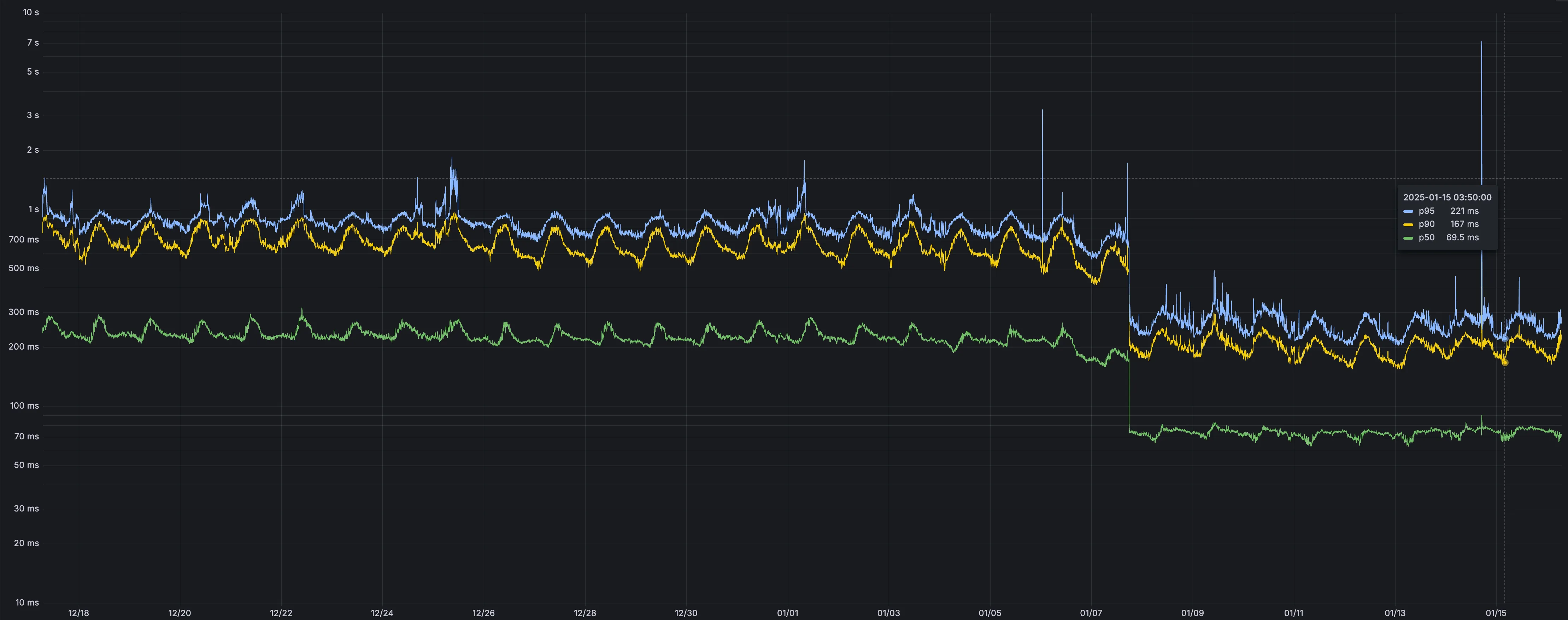
p50, p90, and p95 request latency aggregated across entire D1 service. These latencies are a reference point and should not be viewed as your exact workload improvement.
This performance improvement benefits all D1 Worker API traffic, especially cross-region requests where network latency is an outsized latency factor. For example, a user in Europe talking to a database in North America. D1 location hints can be used to influence the geographic location of a database.
For more details on how D1 removed redundant round trips, see the D1 specific changelog entry.
-
AI Gateway now supports DeepSeek, including their cutting-edge DeepSeek-V3 model. With this addition, you have even more flexibility to manage and optimize your AI workloads using AI Gateway. Whether you're leveraging DeepSeek or other providers, like OpenAI, Anthropic, or Workers AI, AI Gateway empowers you to:
- Monitor: Gain actionable insights with analytics and logs.
- Control: Implement caching, rate limiting, and fallbacks.
- Optimize: Improve performance with feedback and evaluations.

To get started, simply update the base URL of your DeepSeek API calls to route through AI Gateway. Here's how you can send a request using cURL:
Example fetch request curl https://gateway.ai.cloudflare.com/v1/{account_id}/{gateway_id}/deepseek/chat/completions \--header 'content-type: application/json' \--header 'Authorization: Bearer DEEPSEEK_TOKEN' \--data '{"model": "deepseek-chat","messages": [{"role": "user","content": "What is Cloudflare?"}]}'For detailed setup instructions, see our DeepSeek provider documentation.
-

Workers Builds, the integrated CI/CD system for Workers (currently in beta), now lets you cache artifacts across builds, speeding up build jobs by eliminating repeated work, such as downloading dependencies at the start of each build.
-
Build Caching: Cache dependencies and build outputs between builds with a shared project-wide cache, ensuring faster builds for the entire team.
-
Build Watch Paths: Define paths to include or exclude from the build process, ideal for monorepos to target only the files that need to be rebuilt per Workers project.
To get started, select your Worker on the Cloudflare dashboard ↗ then go to Settings > Builds, and connect a GitHub or GitLab repository. Once connected, you'll see options to configure Build Caching and Build Watch Paths.
-
-
Admins can now collect packet captures (PCAPs) and WARP diagnostic logs from end-user devices. For more information, refer to Remote captures.
-
Customers can now have more transparency about their team and user submissions. The new Reclassification tab in the Zero Trust dashboard will allow customers to have a full understanding of what submissions they have made and what the outcomes of those submissions are.
Microsoft 365 customers can now choose to scan all folders or just the inbox when deploying via the Graph API.
-
The latest
cloudflaredbuild 2024.12.2 ↗ introduces the ability to collect all the diagnostic logs needed to troubleshoot acloudflaredinstance. For more information, refer to Diagnostic logs.You can now deploy WARP Connector using a simplified, guided workflow similar to
cloudflaredconnectors. For detailed instructions, refer to the WARP Connector documentation.The new
cloudflaredbuild 2024.10.0 ↗ has a bugfix related to the --grace-period tunnel run parameter.cloudflaredconnectors will now abide by the specified waiting period before forcefully closing connections to Cloudflare's network.
-
Hyperdrive now caches queries in all Cloudflare locations, decreasing cache hit latency by up to 90%.
When you make a query to your database and Hyperdrive has cached the query results, Hyperdrive will now return the results from the nearest cache. By caching data closer to your users, the latency for cache hits reduces by up to 90%.
This reduction in cache hit latency is reflected in a reduction of the session duration for all queries (cached and uncached) from Cloudflare Workers to Hyperdrive, as illustrated below.
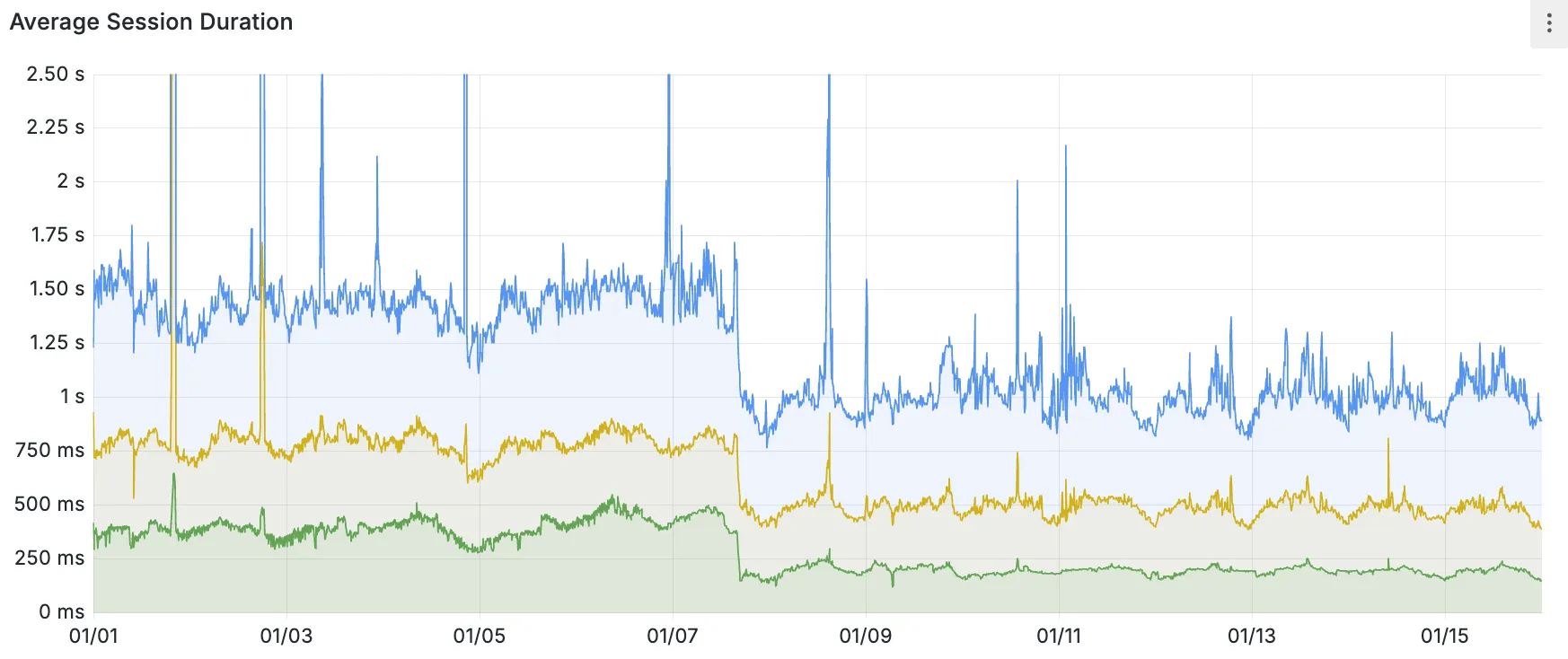
P50, P75, and P90 Hyperdrive session latency for all client connection sessions (both cached and uncached queries) for Hyperdrive configurations with caching enabled during the rollout period.
This performance improvement is applied to all new and existing Hyperdrive configurations that have caching enabled.
For more details on how Hyperdrive performs query caching, refer to the Hyperdrive documentation.
-
Now, you can manage Cloudflare Snippets with Terraform. Use infrastructure-as-code to deploy and update Snippet code and rules without manual changes in the dashboard.
Example Terraform configuration:
resource "cloudflare_snippet" "my_snippet" {zone_id = "<ZONE_ID>"name = "my_test_snippet_1"main_module = "file1.js"files {name = "file1.js"content = file("file1.js")}}resource "cloudflare_snippet_rules" "cookie_snippet_rule" {zone_id = "<ZONE_ID>"rules {enabled = trueexpression = "http.cookie eq \"a=b\""description = "Trigger snippet on specific cookie"snippet_name = "my_test_snippet_1"}depends_on = [cloudflare_snippet.my_snippet]}Learn more in the Configure Snippets using Terraform documentation.
-
Cloudflare's SCIM integrations with Okta and Microsoft Entra ID (formerly AzureAD) are now out of beta and generally available (GA) for all customers. These integrations can be used for Access and Gateway policies and Zero Trust user management. Note: This GA release does not include Dashboard SSO SCIM support.
Admins can now use Access for Infrastructure to manage privileged access to SSH servers. Access for Infrastructure provides improved control and visibility over who accessed what service and what they did during their SSH session. Access for Infrastructure also eliminates the risk and overhead associated with managing SSH keys by using short-lived SSH certificates to access SSH servers.
-
DLP profiles now support setting a confidence level to choose how tolerant its detections are to false positives based on the context of the detection. The higher a profile's confidence level is, the less false positives will be allowed. Confidence levels include Low, Medium, or High. DLP profile confidence levels supersede context analysis.
In addition to logging the payload from HTTP requests that matched a DLP policy in Cloudflare Logs, Enterprise users can now configure a Logpush job to send the entire HTTP request that triggered a DLP match to a storage destination. This allows long-term storage of full requests for use in forensic investigation.
-
Now, you can use Cloud Connector to route traffic to your R2 buckets based on URLs, headers, geolocation, and more.
Example setup:
Terminal window curl --request PUT \"https://api.cloudflare.com/client/v4/zones/{zone_id}/cloud_connector/rules" \--header "Authorization: Bearer <API_TOKEN>" \--header "Content-Type: application/json" \--data '[{"expression": "http.request.uri.path wildcard \"/images/*\"","provider": "cloudflare_r2","description": "Connect to R2 bucket containing images","parameters": {"host": "mybucketcustomdomain.example.com"}}]'Get started using Cloud Connector documentation.
-
You can now use CASB to find security misconfigurations in your AWS cloud environment. You can also connect your AWS compute account to extract and scan your S3 buckets for sensitive data while avoiding egress fees.
-
Gateway users can now create network policies with the Content Categories and Security Risks traffic selectors. This update simplifies malicious traffic blocking and streamlines network monitoring for improved security management.
Gateway users can now generate unique root CAs for their Zero Trust account. Both generated certificate and custom certificate users must activate a root certificate to use it for inspection. Per-account certificates replace the default Cloudflare certificate, which is set to expire on 2025-02-02.
Gateway now offers time-based DNS policy duration. With policy duration, you can configure a duration of time for a policy to turn on or set an exact date and time to turn a policy off.
Gateway now offers new fields in activity logs for DNS, network, and HTTP policies to provide greater insight into your users' traffic routed through Gateway.
-
You can now use the
cacheproperty of theRequestinterface to bypass Cloudflare's cache when making subrequests from Cloudflare Workers, by setting its value tono-store.index.js export default {async fetch(req, env, ctx) {const request = new Request("https://cloudflare.com", {cache: "no-store",});const response = await fetch(request);return response;},};index.ts export default {async fetch(req, env, ctx): Promise<Response> {const request = new Request("https://cloudflare.com", { cache: 'no-store'});const response = await fetch(request);return response;}} satisfies ExportedHandler<Environment>When you set the value to
no-storeon a subrequest made from a Worker, the Cloudflare Workers runtime will not check whether a match exists in the cache, and not add the response to the cache, even if the response includes directives in theCache-ControlHTTP header that otherwise indicate that the response is cacheable.This increases compatibility with NPM packages and JavaScript frameworks that rely on setting the
cacheproperty, which is a cross-platform standard part of theRequestinterface. Previously, if you set thecacheproperty onRequest, the Workers runtime threw an exception.If you've tried to use
@planetscale/database,redis-js,stytch-node,supabase,axiom-jsor have seen the error messageThe cache field on RequestInitializerDict is not implemented in fetch— you should try again, making sure that the Compatibility Date of your Worker is set to on or after2024-11-11, or thecache_option_enabledcompatibility flag is enabled for your Worker.- Learn how the Cache works with Cloudflare Workers
- Enable Node.js compatibility for your Cloudflare Worker
- Explore Runtime APIs and Bindings available in Cloudflare Workers
-
Workflows is now in open beta, and available to any developer a free or paid Workers plan.
Workflows allow you to build multi-step applications that can automatically retry, persist state and run for minutes, hours, days, or weeks. Workflows introduces a programming model that makes it easier to build reliable, long-running tasks, observe as they progress, and programatically trigger instances based on events across your services.
You can get started with Workflows by following our get started guide and/or using
npm create cloudflareto pull down the starter project:Terminal window npm create cloudflare@latest workflows-starter -- --template "cloudflare/workflows-starter"You can open the
src/index.tsfile, extend it, and usewrangler deployto deploy your first Workflow. From there, you can:- Learn the Workflows API
- Trigger Workflows via your Workers apps.
- Understand the Rules of Workflows and how to adopt best practices
-
It’s now easy to create wildcard-based URL Rewrites. No need for complex functions—just define your patterns and go.
What’s improved:
- Full wildcard support – Create rewrite patterns using intuitive interface.
- Simplified rule creation – No need for complex functions.
Try it via creating a Rewrite URL rule in the dashboard.
-
Gateway users on Enterprise plans can create HTTP policies with file sandboxing to quarantine previously unseen files downloaded by your users and scan them for malware.
Gateway users on any plan can now use the PDNS threat intelligence feed provided by the UK National Cyber Security Centre (NCSC) in DNS policies.
Gateway users can now select which endpoints to use for a given DNS location. Available endpoints include IPv4, IPv6, DNS over HTTPS (DoH), and DNS over TLS (DoT). Users can protect each configured endpoint by specifying allowed source networks. Additionally, for the DoH endpoint, users can filter traffic based on source networks and/or authenticate user identity tokens.
-
Now, you can create common rule configurations in just one click using Rules Templates.
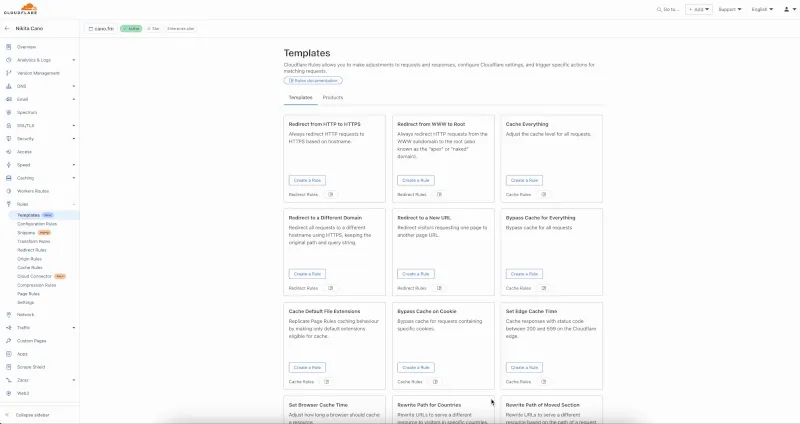
What you can do:
- Pick a pre-built rule – Choose from a library of templates.
- One-click setup – Deploy best practices instantly.
- Customize as needed – Adjust templates to fit your setup.
Template cards are now also available directly in the rule builder for each product.
Need more ideas? Check out the Examples gallery in our documentation.
-
You can now upload files with multiple columns of data as Exact Data Match datasets. DLP can use each column as a separate existing detection entry.
-
Admins can now configure Zero Trust seats to automatically expire after 1 month of user inactivity. The previous minimum was 2 months.
-
Email Security is now live under Zero Trust.
Customers using Microsoft Office 365 can set up Email Security via Microsoft Graph API.
-
macOS users can now download
cloudflared-arm64.pkgdirectly from GitHub ↗, in addition to being available via Homebrew.
-
Gateway now offers the ability to selectively ignore CNAME domain categories in DNS policies via the Ignore CNAME domain categories setting in the policy builder and the
ignore_cname_category_matchessetting in the API.Gateway now offers a more extensive, categorized list of files to control uploads and downloads.
-
You can now exchange user risk scores with Okta to inform SSO-level policies.
You can now configure a predefined risk behavior to evaluate user risk score using device posture attributes from the SentinelOne integration.
-
Applications now load more quickly for customers with a large number of applications or complex policies.
Access admins can defer all CORS enforcement to their origin server for specific Access applications.
All user identity changes via SCIM or Authentication events are logged against a user's registry identity.
-
You can now scan your Bitbucket Cloud workspaces for a variety of contextualized security issues such as source code exposure, admin misconfigurations, and more.
You can now scan your Box and Dropbox files for DLP matches.
You can now export all top-level CASB findings or every instance of your findings to CSV.
-
You can now scan your Box and Dropbox files for DLP matches.
DLP can now detect sensitive data in jpeg, jpg, and png files. This helps companies prevent the leak of sensitive data in images, such as screenshots.
-
Admins can view the last ISP seen for a device by going to My Team > Devices. Requires setting up a traceroute test.
Admins can now set DEX alerts using Cloudflare Notifications. Three new DEX alert types:
- Device connectivity anomaly
- Test latency
- Test low availability
-
Removed dependency on third-party cookies in the isolated browser, fixing an issue that previously caused intermittent disruptions for users maintaining multi-site, cross-tab sessions in the isolated browser.
-
Access for SaaS applications can be setup with OIDC as an authentication method. OIDC and SAML 2.0 are now both fully supported.
Allow users to log in to Access applications with their WARP session identity. Users need to reauthenticate based on default session durations. WARP authentication identity must be turned on in your device enrollment permissions and can be enabled on a per application basis.
-
All new Access for SaaS applications have unique Entity IDs. This allows for multiple integrations with the same SaaS provider if required. The unique Entity ID has the application audience tag appended. Existing apps are unchanged.
Allows Access admins to set a default relay state on Access for SaaS apps.
-
Access admins can now tag applications and allow users to filter by those tags in the App Launcher.
Allow Access admins to configure the App Launcher page within Zero Trust.
Access admins can now view the full contents of a user's identity and device information for all active application sessions.
Access admins can now add custom claims to the existing named IdP providers. Previously this was locked to the generic OIDC provider.
Support Azure AD authentication contexts directly in Access policies.
-
Allow Access admins to customize the block pages presented by Access to end users.